Phishing Messages
This page is designed to give an overview of what constitutes a phishing message, what kind of information Technology Services and other CCA offices will ask for via email, how to identify a phishing message, and what to do if you think your email account has been compromised.
Phishing Emails
What is a Phishing Email?
A phishing email is any email that purports to be from a legitimate source, but is seeking to solicit confidential information from the recipient for malicious purposes. Most often, the perpetrators of the email scheme are attempting to acquire information like Social Security Numbers, bank account numbers, bank PINs, birthdates, student ID numbers, or email and website passwords. This information, once obtained, is used for identity theft and fraud.
We Won't Ask!
Tech Services and other CCA offices will never ask for confidential information via email. CCA offices have access to your confidential information on a need-to-know basis. If someone at the college needs to know, we have records in which to look up the information. There is no administrative or technical reason we will ever need your password for any kind of account management or maintenance
How to Identify Phishing
While some spam may be very convincing, there are usually several markers to help you identify phishing messages.
- From unknown address: If you receive an email purporting to be from CCA, but it comes from an address other than something@cca.edu, it's likely not from CCA. All official CCA email should come from CCA email accounts. Certainly, any communication from Tech Services will come from a CCA email account.
- Asks for confidential information: As mentioned above, Tech Services and other CCA offices will never ask for your confidential information via email. This includes SSN, passwords, and bank account information.
- Grammatical errors: Often, though not always, phishing messages will have obvious grammatical errors or spelling errors. These errors can be a clue that the message hasn't come from a legitimate source.
- Threats / Immediacy: Phishing messages often try to encourage you to reply by threatening to close your bank or email account if you don't reply immediately.
- Suspicious links: One of the ways phishers can perpetrate identity theft is by redirecting you to websites you don't intend to visit. Phishing messages will often contain a link that directs your browser to a fake website that aids in obtaining your confidential information.
What to Do
If you don't know whether an email is legitimate, the first step is to leave it alone! Don't reply to the message, and don't click on any links in the message. Taking time to think about the message and your actions can help prevent the theft of your identity, bank accounts, email accounts, and student records!
You can report spam and phishing messages in CCA Gmail (you must be logged in to Gmail, not using an email program):
- First, click on the down-arrow to the right of the REPLY button
- In the drop-down, click on REPORT PHISHING (for phishing messages)
- For regular spam, click on REPORT SPAM
When you do this, it notifies Google who will report it to the authorities and also mark the message as spam automatically for other folks who receive it.
Finally, if you have responded to a phishing message, please contact the Help Desk immediately. Tech Services can assist you in resetting your password and ensuring access to your account is secured.
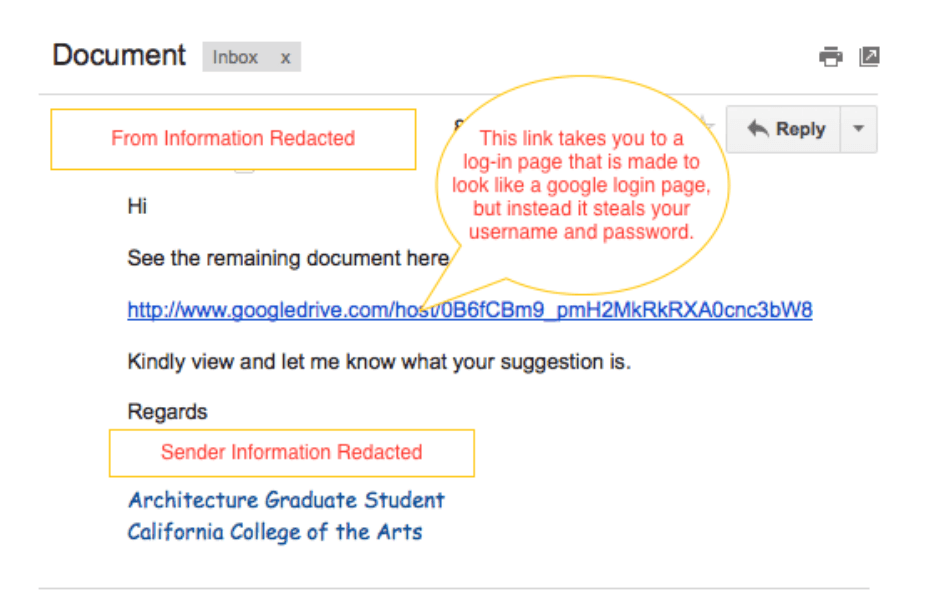
Example of a Phishing Message Using Google Drive
While most phishing scams are identifiable by the use of false URLs, bad grammar, and phony logos, this one works within Google Drive itself, so appeared to be legitimate (even the security certificate is correct). When accessed, the user is prompted by a false Google login dialog which captures credentials behind the scenes.
Luckily, one of our users reported it to the Help Desk and we were able to quickly identify the message’s recipients.
Annotated Phishing Message Example:
If you believe you may have fallen for a phishing attempt, please contact the CCA Help Desk immediately at helpdesk@cca.edu, or call 510.594.5010.
Example of a Phishing Message
The example below has a number of things that are easy to spot, if you look.
Phishing Example:
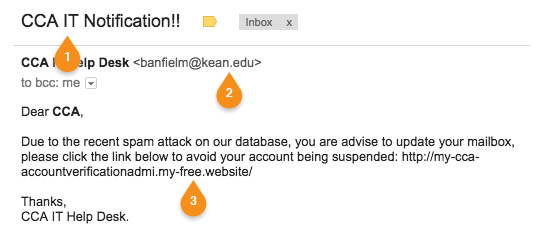
- There isn't an "IT" department at CCA. We're Technology Services (or Tech Services). And, frankly, two exclamation points isn't really our style.
- The email comes from a domain other than "cca.edu". Unfortunately, this is really easy from someone to fake so don't rely on the sender's domain as your only clue.
- The link that you're asked to click on is also not a "cca.edu" web site.
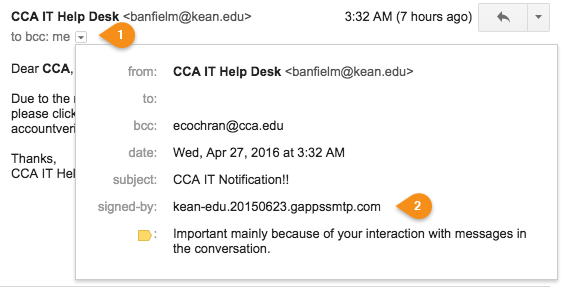
But the best indicator of all can be found by clicking the "Show detail" dropdown in the email header. Check the "signed by" item in the dropdown. Email from the Tech Services department at CCA will always say "signed by: cca.edu".
Fake signature on phishing email.
Properly signed email from real cca.edu staff.
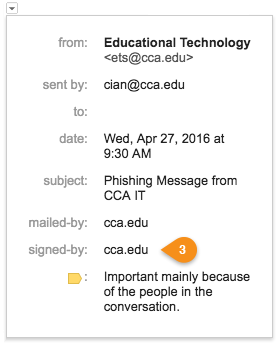
- Show details drop-down.
- Not signed by CCA.edu.
- What you should see if the email is legitimately from CCA.
Technology Services has observed a trend of fraudulent SMS-text messaging or “smishing attacks” among educational organizations.
Smishing Messages
What is Smishing?
Smishing, a combination of "SMS" and "Phishing," is a deceptive technique used by cybercriminals to trick individuals into revealing sensitive information or downloading malicious content via text messages. These messages often appear to be from legitimate sources, such as banks, government agencies, service providers, or a CCA department creating a false sense of urgency and trust.
How Smishing Works
The perpetrators behind smishing attacks craft convincing messages that prompt recipients to click on malicious links, accept Duo attempts, or disclose personal information, such as passwords, financial details, or account credentials. These texts may also encourage users to call a seemingly genuine number, which connects them to a fraudulent support center, further perpetuating the deception.
Example of Smishing
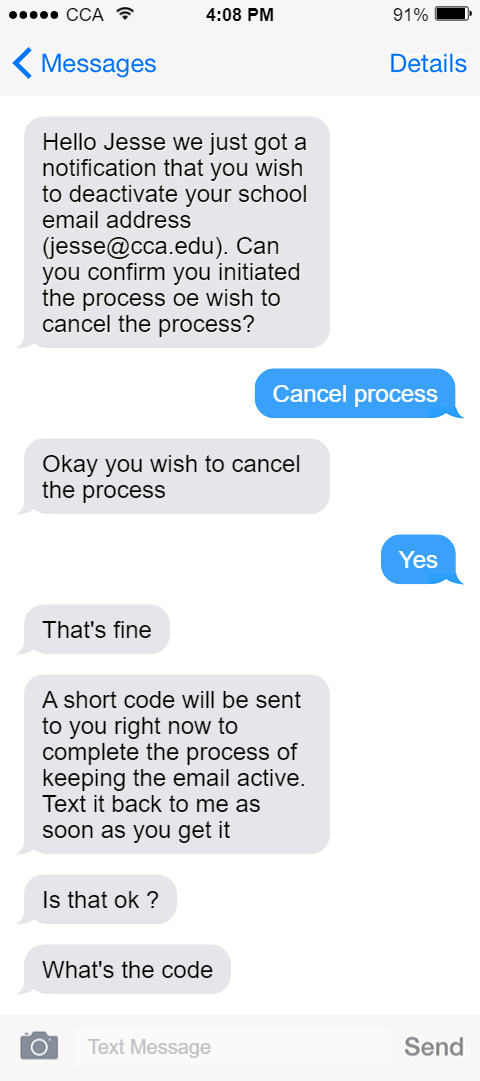
Protecting Yourself from Smishing Attacks:
- Be Vigilant: Remain cautious of unsolicited messages, especially those requesting urgent actions or personal information. Verify the authenticity of the sender before taking any action.
- Don't Click, Don't Share, Don’t Scan, Don’t Duo: Refrain from clicking on links, sharing sensitive data through text messages, accepting Duo logins that you didn’t initiate, or scanning any QR codes on messages. Legitimate organizations usually don't request such information via SMS.
- Double-Check URLs: If you receive a link in a text message, manually verify its legitimacy by visiting the official website of the organization in question.
- Update Software Regularly: Keep your mobile devices' software and apps up-to-date to patch potential security vulnerabilities.
- Report Suspicious Messages: If you suspect a smishing attempt, report it to the Technology Services help desk to help us combat such scams.
More Info:
- Stay Safe Online The National CyberSecurity Alliance builds strong public/private partnerships to create and implement broad reaching education and awareness efforts to empower users at home, work and school with the information they need to keep themselves, their organizations, their systems, and their sensitive information safe and secure online and encourage a culture of cybersecurity.
- Stop. Think. Connect. is a national public awareness campaign aimed at increasing the understanding of cyber threats and empowering the American public to be safer and more secure online. Cybersecurity is a shared responsibility. We each have to do our part to keep the Internet safe. When we all take simple steps to be safer online, it makes using the Internet a more secure experience for everyone.
- Technology Services Policies CCA technology policies.